Top Security Challenges in Embedded Systems and How to Overcome Them
2 September 2024
2 September 2024
Security is becoming one of the most critical concerns in the current embedded solutions market – and for a valid reason. With the advancement of technology, computer systems are exposed to an increasing number of potential threats. Embedded systems are particularly vulnerable to cyberattacks due to their frequent deployment in settings where traditional network defences, such as firewalls and other security tools, are absent.
Moreover, the upcoming implementation of the EU Cyber Resilience Act will further highlight the importance of robust security measures. However, it is worthwhile to start strengthening defence mechanisms now, rather than wait for the regulation to take effect.
In this article, we will delve into some of the most common security challenges facing embedded systems and learn how to successfully overcome them.

Although we may not notice, embedded systems are all around us, constantly present in our daily lives. Whether it is your coffee machine, smartwatch or even traffic lights – none of them could function without an embedded system. As technology develops, so does the popularity of embedded systems, which are becoming an essential component of many devices. Researchers project that the global embedded systems market will grow from $100.04 billion in 2023 to $161.86 billion by 2030.
However, this growth is also leading to increased security challenges, particularly with the rise of IoT devices. Their connection to the internet as well as each other makes them especially vulnerable to potential data breaches, unauthorized access and system takeovers. Additionally, embedded systems, which are often customized and created for a specific device, usually lack typical protections such as firewalls, making them relatively easy targets for hacking attacks. This is particularly concerning as many of these devices gather sensitive data that could be leaked in case of an attack.
Moreover, in the case of IoT devices, an attack on a single device can put the whole system at risk. For example, without proper protection, a hacker can infiltrate the security system and take control of an entire smart home by attacking just one device. This could enable the attacker to obtain private information about the household and even spy on or interfere with residents’ lives.
Unfortunately, in the past, embedded security was often neglected due to the misconception that those systems are not an appealing target for hackers. Consequently, their protection often came down to merely setting a password. Meanwhile, with the emergence of AI and cloud-based applications, and the increasing device connectivity, the number of attack vectors is growing and new threats are arising, forcing developers to take security more seriously than ever.

Embedded systems can be targeted through software, hardware, and network, presenting multiple possibilities for cybercriminals. To ensure comprehensive protection, it is essential to secure the device at every possible level. Focusing on only one aspect and neglecting others can result in exposing the system to significant threats. Therefore, security measures should be incorporated throughout the entire development process, from design to implementation and testing. However, to effectively secure the device, it is essential to have a proper understanding of potential threats that embedded systems may face.
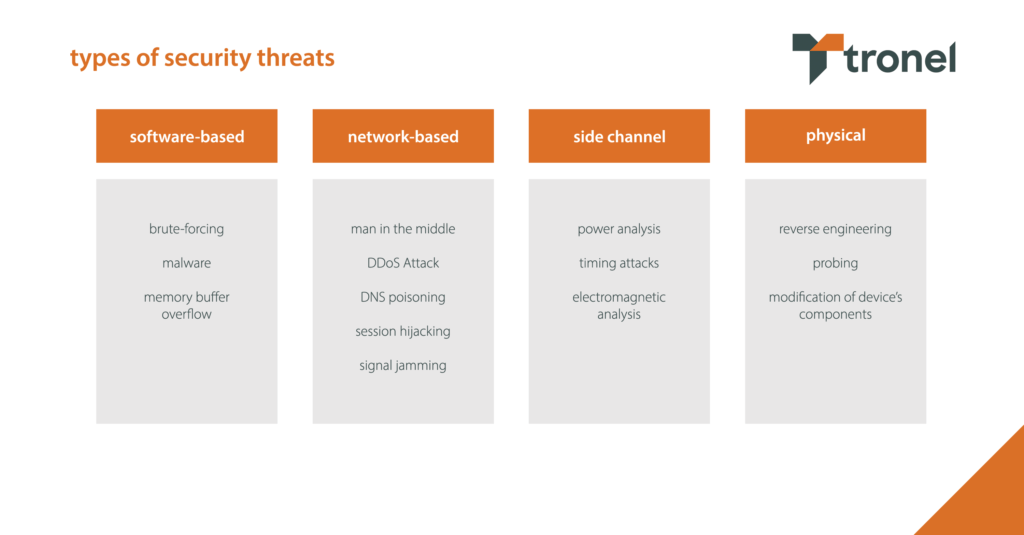
Software is the most popular target for cyberattacks due to its relative accessibility and potential for remote attacks. Software-based intrusions usually don’t require the hacker to have in-depth technical knowledge of the device or the system. Attackers exploit vulnerabilities in the security and design of an operating system to gain control of the system and access stored data.
The most common methods include brute-forcing attacks, malware injection through fake updates or security patches, and memory buffer overflow. Brute-forcing attacks involve attempting to gain access to a system by guessing the access credentials. Meanwhile, during memory buffer overflow hackers overwhelm the system’s memory buffer with too much data which contains exploits that enable attackers to gain credentials and elevate their access rights. If successful, those attacks can result in data loss, disruption of the device’s functionality, and unauthorised access to the device.
The high level of device connectivity to the network creates enormous opportunities for hackers. Attackers target embedded device’s communication channels to intercept, modify, or disrupt transmitted data. Like software attacks, network-based attacks can also be executed remotely.
Some of the most common methods hackers use include man-in-the-middle attacks and Distributed Denial of Service (DDoS) attacks. The former involves altering the connection parameters of two devices in order to insert a third one between them, giving the attacker the ability to eavesdrop. A DDoS attack, on the other hand, involves flooding the system with requests from many different sources, making it inaccessible. Other network-based attacks also include DNS poisoning, session hijacking or signal jamming.
This type of attack requires physical access to the device, making it more difficult to execute compared to previous ones. However, with the devices often being deployed in public places, many times unprotected, it can be significantly easier for the hacker to tamper with them.
Physical attacks include theft, probing, reverse engineering, or modifying the device’s components to extract sensitive information or compromise its functionality.
Side channel attacks focus on exploiting hardware security loopholes. These attacks are the hardest to execute as they require both physical access to the device, as well as significant knowledge of the system and hardware design.
They include power analysis, timing attacks, and electromagnetic analysis. These methods allow hackers to gain valuable data about the internal operations of the system by monitoring changes in power consumption, using information about the timing of operations, and recording and analyzing emissions from the device. As a result, attackers can steal cryptographic keys and even gain control of the system.

Due to their unique characteristics – including limited resources, long lifespan and deployment in public spaces – embedded systems can be quite difficult to secure. Below we outline some of the key challenges facing embedded security.
Embedded devices are usually designed to operate for many years, often running on the same system. This means that developers need to consider all possible threats, even those that have not yet emerged. Focusing solely on present challenges can leave the system vulnerable to future risks.
The longevity of the device is also linked to challenges in ensuring that the system remains up to date. Embedded systems are often not designed with updates in mind, and consequently, many manufacturers don’t even provide a possibility to safely update the system. Meanwhile, as technology advances, new threats are constantly emerging, making outdated operating systems prime targets for cyberattacks.
More and more devices are becoming connected to the internet, communicating and transmitting data across the network. This increased connectivity enhances the functionality of devices and makes life easier for users with systems such as smart home. However, it also expands the attack surface, making the embedded systems vulnerable to various cyber threats such as remote hacking and DDoS attacks.
Due to the extensive communication between embedded systems, it is crucial to ensure that all communication comes from a trusted source. Weak passwords and poorly implemented authentication mechanisms can be easily exploited by attackers leading to unauthorized access and potential data breaches.
Embedded systems face significant memory and storage constraints, and therefore require thoughtful optimization and efficient resource management. This makes it extremely challenging to implement effective security measures that can operate throughout the device’s lifespan.
Encryption plays a crucial role in safeguarding sensitive data transmitted and stored by embedded systems. However, using weak encryption algorithms or improperly implementing encryption mechanisms can render the system vulnerable to various attacks, such as eavesdropping and data manipulation.
Embedded devices are often deployed in remote or public spaces, where they are easily accessible to potential attackers. This puts them at risk of physical tampering or direct attacks, including data theft or sabotage.

Ensuring the security of embedded systems is a multifaceted endeavour, that requires a comprehensive approach encompassing various strategies, and practices. Manufacturers must remember to secure all the possible attack surfaces, including software, firmware, hardware and network.
In any embedded project security should always come first. It must be considered and treated as a priority, not as a last-minute add-on. This means we should integrate security measures from the earliest stages of system design and development, addressing all the possible threats and vulnerabilities before the deployment. This helps define and prevent any loopholes in embedded security before they become a potential issue in the future.
Regular and automated updates are crucial in securing the system against known and emerging threats. By providing mechanisms for secure and authenticated update delivery, manufacturers can ensure that only genuine updates from trusted sources are installed on embedded devices. Additionally, implementing rollback mechanisms allows for reverting to previous versions in case of update failures, ensuring system stability and continuity of operations. See our insights on over-the-air firmware updates.
The secure boot process plays a pivotal role in safeguarding embedded devices against unauthorized modifications and malicious code injection. By verifying digital signatures before executing firmware and software, the boot process ensures that only trusted code is loaded during system startup. This defence mechanism protects the integrity of the device’s firmware and software and prevents the tampering of the system.
Sometimes, certain devices have access to features they don’t need, which is not only unnecessary but also extremely dangerous. This can create opportunities for hackers who can obtain access to the system by hacking one of the devices. By restricting access to only essential resources and functionalities, manufacturers can significantly reduce the risk of unauthorized activities and data breaches, enhancing the overall security of the system.
Effective encryption and decryption mechanisms are essential for protecting sensitive data stored and transmitted by embedded systems. Using strong encryption algorithms and adhering to best key management practices ensure the confidentiality and integrity of data. Additionally, isolating critical hardware functions prevents unauthorized access to important data, even if other parts of the hardware are compromised.
To prevent data interception and tampering, embedded systems should only accept communication from trusted and authenticated sources. Implementing secure communication protocols and encrypting data transmissions protects sensitive information from eavesdropping and man-in-the-middle attacks. Additionally, the systems should be equipped with firewalls and strong authentication mechanisms and minimize all external communication to only what is necessary.
Even after deploying all the security measures, we shouldn’t leave the system by itself. Continuous monitoring of device logs, network activity, and system performance is essential for detecting anomalies and potential security breaches in real time. Regular security assessments and audits help identify vulnerabilities, ensure compliance with industry standards, and address security gaps before they can be exploited by attackers.
It is vital to ensure that all embedded systems remain compliant with current industry standards, including ISO/IEC 27001, which outlines requirements for information security management systems, IEC 62443, and NIST SP 800–53. Organizations should also pay close attention to emerging legislation, such as the EU Cyber Resilience Act. Taking these actions not only helps avoid potential legal repercussions but also ensures that the system is effectively safeguarded against the latest threats.

In March 2024 European Parliament approved the new Cyber Resilience Act which will strongly influence all products with digital elements, including embedded devices. The regulation aims to guarantee the security, resilience against cyber threats, and provision of sufficient information regarding the security features of the products. This includes ensuring that all devices receive automated security updates independent of functional updates. The implementation of the EU Cyber Resilience Act is intended to enhance security in all the products connected directly or indirectly to another device or network.
This upcoming regulation only underscores the importance of prioritizing security, emphasizing the need to take it seriously. By implementing the strategies outlined above, we can significantly reduce the risk of cyberattacks and protect embedded systems against present and emerging threats, ensuring a safer future for embedded technologies.
Ready to enhance your embedded system’s security and efficiency? Maybe looking for embedded Linux development or firmware engineering services?
Contact us to discuss how our experts can support you in creating innovative solutions that meet the highest standards of security and performance.
By Anna Kazarnowicz

